Zero Day Vulnerabilities, Man In The Middle Attacks, Worms, Exploits, Phishing, Hacked accounts, and the list goes on and on. The fact is that computer users in today’s world are facing a growing threat from outside sources when using the internet. Most people are not aware, nor care about these threats, that is, until it is too late. But why and how is this happening? What are we doing about it? and Where do we go from here? All valid questions, that really do not have a solid, absolute answer.
 We hear almost everday about new threats, either that are attacking an unknown exploit (Zero Day Attack), or of horror stories regarding account hacks and phishing scams. Windows, Adobe, Apple, and just about every other major software creator has faced this issue at least once, some many, many times. In the early days of hacking, viruses were mearly a proving ground, a gold star for a lapel, for many young and very talented software writers. No malicious intend, for the most part was ever meant. All they wanted to see, is who’s virus could propogate the fastest and to the greatest extend. It was a game to them, albeit a very annoying one. However, those days are long gone, and the occasional malicious software written by a teen with a chip on his/her shoulder are no longer of a concern. Today, these onslaughts are being carried out by large criminal organizations, who do have malicious intent, and have found out that these scams and attacks are also very lucrative. What’s worse, is the people doing this are extremely talented and savvy software creators who are constantly deriving new ways in order to get deeply into the pockets of the ordinary computer user.
We hear almost everday about new threats, either that are attacking an unknown exploit (Zero Day Attack), or of horror stories regarding account hacks and phishing scams. Windows, Adobe, Apple, and just about every other major software creator has faced this issue at least once, some many, many times. In the early days of hacking, viruses were mearly a proving ground, a gold star for a lapel, for many young and very talented software writers. No malicious intend, for the most part was ever meant. All they wanted to see, is who’s virus could propogate the fastest and to the greatest extend. It was a game to them, albeit a very annoying one. However, those days are long gone, and the occasional malicious software written by a teen with a chip on his/her shoulder are no longer of a concern. Today, these onslaughts are being carried out by large criminal organizations, who do have malicious intent, and have found out that these scams and attacks are also very lucrative. What’s worse, is the people doing this are extremely talented and savvy software creators who are constantly deriving new ways in order to get deeply into the pockets of the ordinary computer user.
For most, all that is wanted, is to turn on the computer and get email, check accounts, and do some online shopping. Security, although they care about it, is something that most users do not want to know any of the juicy details behind how it works, and what dangers to look for. They simply want a machine that works and is safe to use. Unfortunately, that is not the way of today’s computing. Even so, simple is better to most users. SSL/TLS, file encryption, WPA2, and the like are all things that the ordinary computer user does not want to know about, or even care about. And quite frankly, why should they? Computer offectionado’s thrive on this sort of stuff, but for the normal user……no!!! The casual user knows that an anti-virus software will keep them safe. Some may even use an additional anti-malware scanner, but will rarely use it to fully scan the computer. Firewall…..I know I need one, but what is it? But even with these tools, our computers are still not safe from becoming compromised.
The major anti-virus companies will all admit that this is a hurry, and catch-up game. The bad guys always seem to be one step ahead of the good guys, sometimes quite a few steps ahead actually. The AV manufacturers are always trying to lessen this lead, but like I said earlier, this is no teen with a bad attitude, these are savvy, technical, and treacherous organizations that are making our life online hell. A new bug is released into the ‘wild”, now it will take the anti-malware companies time to find it, reverse engineer it, and then launch a fix for it. Heuristics have helped in this matter, but have also created some new problems, namely false positives. Heuristics is a method of scanning your computer in which the anti-malware software is not looking for specific malware, but are only looking for malware-like activity, such as registries being changed. As a result, false positives are becoming more prevelant, in which the anti-malware falsely labels a vulnerability, when it is really a legitimate act. Holes/vulnerabilities that are found in software, and then are issued fixes through software updates, are still being exploited, due to the average user not knowing enough or caring to get the update. Time is expensive, and updating software can be time consuming, and all the user wants to do is turn the machine on, do what they need to do, and move on to the their next agenda. Look at the conficker worm, a patch and a fix for this bug was issued long ago (Oct 2008) and yet, it is still out there.
So where do we go from here?
Well, short of turning off the internet, re-working the entire infrastructure, and then turning it back on again, we have only a limited amount of tools at our luxury. However, the strongest of these is education. The word has got to be spread throughout the computer world the need to protect one’s self while on the internet. I certainly do not mean that everyone needs to become a computer security guru, but general knowledge of things to look for would definitely not make it so easy for the bad guys to get in. Even then, it is still going to be happening. Their is money to be made, and like I said earlier, these bad guys have found out that there is a ton of it to be scammed.
In the end, this is the way it is, and appears to be the way that it will remain in the immediate future. In fact, the chances are, that it is going to get more volatile out there. The one true weapon that we all have to battle this armegeddon on the internet, is our ability to use common sense. That is our most powerful weapon, without it, we are doomed. Add a small dose of knowledge, and we could vastly hamper these attempts in ruining our lives. We need to keep our critical personal data safe and secure, knowing what is OK to become public knowledge and what could hurt us is paramount. I would never post my banking information on the internet, although many people have clicked on links in emails stating that their accounts have problems, and enter banking credentials. You may as well have posted it directly to the public internet. It is things like this, that make it easier for the bad guys to successfully do what they do. A pound of common sense, coupled with a sprinkling of knowledge is out greatest weapon.
What Are Your Thoughts??


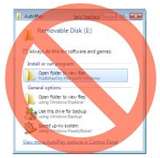
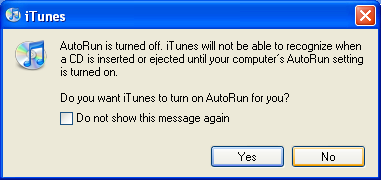
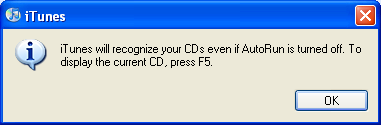
 This piece may, quite frankly, be of absolutely no interest to many of you as most do not even know what this is. I believe that the AutoRun feature in Windows is a huge security risk, especially since the Conficker hub-a-bah-loo. But now, don’t let me get a head of myself. First things first….
This piece may, quite frankly, be of absolutely no interest to many of you as most do not even know what this is. I believe that the AutoRun feature in Windows is a huge security risk, especially since the Conficker hub-a-bah-loo. But now, don’t let me get a head of myself. First things first…. Just a reminder!!!! Today, 5/12/09 is “Patch Tuesday”. The second Tuesday of every month is the day when the monthly security and software updates become available for your Windows machine. It is critical that these updates are done each and every month. The Conficker worm is a prime example of how important these updates are. If all Windows machines had been updated in October, the Conficker worm would probably not have propagated so efficiently. Anyway, you should have Automatic Updates turned on, on your machine, so that all critical updates are automatically downloaded and installed on your machine. It is recommended that you turn the “Automatic Updates” on as there are times when “Out of Sequence” updates occur mid-way through the month, and if you do not have them turned on and do not manually check weekly, you will miss the critical update, and by the time you manually get them, it may be too late. But, it you don’t have “Automatic Updates” turned on (or are not sure whether you do or not), then you must go to Microsoft’s website and download them manually. To get your updates manually, click
Just a reminder!!!! Today, 5/12/09 is “Patch Tuesday”. The second Tuesday of every month is the day when the monthly security and software updates become available for your Windows machine. It is critical that these updates are done each and every month. The Conficker worm is a prime example of how important these updates are. If all Windows machines had been updated in October, the Conficker worm would probably not have propagated so efficiently. Anyway, you should have Automatic Updates turned on, on your machine, so that all critical updates are automatically downloaded and installed on your machine. It is recommended that you turn the “Automatic Updates” on as there are times when “Out of Sequence” updates occur mid-way through the month, and if you do not have them turned on and do not manually check weekly, you will miss the critical update, and by the time you manually get them, it may be too late. But, it you don’t have “Automatic Updates” turned on (or are not sure whether you do or not), then you must go to Microsoft’s website and download them manually. To get your updates manually, click  Conficker, aka Downadup seems to have awoken and has become active. After the hype created on April 1st, it appears that the worm has waited 1 week, as on Wednesday April 8th it reared it’s ugly head. We all new that a piece of code that is so expertly written, albeit devious at the same time, was not just going to sit there and do nothing. It now appears that things are starting to happen.
Conficker, aka Downadup seems to have awoken and has become active. After the hype created on April 1st, it appears that the worm has waited 1 week, as on Wednesday April 8th it reared it’s ugly head. We all new that a piece of code that is so expertly written, albeit devious at the same time, was not just going to sit there and do nothing. It now appears that things are starting to happen. for more computers connected to the internet that may not have received Microsoft’s critical update in October. Also by using Conficker’s P2P (Peer To Peer) technology, it will be able to contact other infected host computers, which may not have received the new “instructions” on April 1st, and can then update them with the current variant. This test is supposed to end on May 3rd at which time it may sit and wait for new instructions on what it should do next. At that time it will delete any trace that it had ever been there in the first place. No files, no registries, no nothing, however it will remain on the infected computer and will just sit quietly awaiting new commands from it’s master.
for more computers connected to the internet that may not have received Microsoft’s critical update in October. Also by using Conficker’s P2P (Peer To Peer) technology, it will be able to contact other infected host computers, which may not have received the new “instructions” on April 1st, and can then update them with the current variant. This test is supposed to end on May 3rd at which time it may sit and wait for new instructions on what it should do next. At that time it will delete any trace that it had ever been there in the first place. No files, no registries, no nothing, however it will remain on the infected computer and will just sit quietly awaiting new commands from it’s master. Remember Downadup, aka Conficker? I posted about it a couple of months ago, when it first became news. Well now the thing has become even bigger news. The Downadup worm that I wrote about was the first version of this worm. Well now it has mutated, so to speak. Downadup initially became news when it quickly infected over 11 million computers, and when I say quickly, I mean within a week. And mind you, the spread of this worm was because of computers that, for whatever reason, were not updated with Microsoft’s latest updates back in October 2008. Well a concerted effort to track this worm down and shut it down by anti-virus vendors was initiated. Now not to fault the cause, this effort probably caused a mutation of this worm to what was known as Downadup B. When this version was reverse engineered, it was found to have a data base of around 250 websites in which it was to use to “phone home”, on February 12th, in order to get further instructions on what it was supposed to do. Once this was discovered, quick action was taken to shut these domains down, thus not allowing the worm to phone home.
Remember Downadup, aka Conficker? I posted about it a couple of months ago, when it first became news. Well now the thing has become even bigger news. The Downadup worm that I wrote about was the first version of this worm. Well now it has mutated, so to speak. Downadup initially became news when it quickly infected over 11 million computers, and when I say quickly, I mean within a week. And mind you, the spread of this worm was because of computers that, for whatever reason, were not updated with Microsoft’s latest updates back in October 2008. Well a concerted effort to track this worm down and shut it down by anti-virus vendors was initiated. Now not to fault the cause, this effort probably caused a mutation of this worm to what was known as Downadup B. When this version was reverse engineered, it was found to have a data base of around 250 websites in which it was to use to “phone home”, on February 12th, in order to get further instructions on what it was supposed to do. Once this was discovered, quick action was taken to shut these domains down, thus not allowing the worm to phone home.